
The Web is not just about business and big money. Billions of pages and blog posts are written every day, every second, by small website owners and bloggers looking to share their views with the world. This is what makes the charm of the Web: it offers a space of relative freedom for everyone.
But the Internet is also a wild jungle that harbors many dangers. No one is really safe from a hack, a DDOS attack or a virus. If you run a small business on the Internet, you know how important the security of your website and online transactions is. It is important to know how to secure your website!
This is a really crucial aspect to consider when planning your website launch: how can I secure my content and work from external threats? How can I offer the best possible user experience to my visitors? These are questions you should ask yourself every time you update your website.
Our 9 tips for securing your website
Securing a site is not necessarily within everyone’s reach, but that does not mean that you absolutely have to be a programmer or a computer scientist to get there.
So we’ve listed 9 tips that are both easy to apply and detailed enough to pique your curiosity about basic security issues, so that you slowly but surely become your own web security expert.
All advice is hack specific and we’ll also walk you through techniques you can use to test your website for security vulnerabilities. Don’t worry: nothing too complicated, but it’s important that you familiarize yourself with the simple tools and techniques that can block or repel attacks, for the good of your projects.
Tip #1: Use Complex Passwords
Web security experts use many methods to ensure optimal security of the web systems and transactions they work on: public key cryptography, chains of trust, signatures, SSL and TSL (Transport Layer Security).
It all starts with choosing your passwords!
- Use a strong password generator to get a hard-to-crack password, including alphanumeric characters and special symbols. The more the symbols are random or pseudo-random (i.e. they are not connected to each other and all symbols have an equal chance of succeeding each other), the more secure the password.
- Use a password manager like Dashlane, LastPass, Password Safe (Windows only) or Password Gorilla to save and encrypt all your passwords, which you can unlock with a Master Password, one password to control them all.

Tip #2: Pay attention to your scripts and plugins
It is well known that website scripts and CMS platforms are the main vehicles for hacking attacks.
If you host scripts written in PHP, ASP, and JavaScript, be aware that they may have security holes and bugs that their developers might have overlooked.
In addition to contacting the developer immediately upon discovering any of the issues mentioned above, there are non-technical methods you can use to ensure that your scripts won’t give you trouble in the long run:
- Read your script’s release document carefully: it often contains details about fixes and bug fixes.
- Watch for warnings from your software installer, control panel, or even Google Webmaster Tools: if you need to update or edit/delete a file, do so.
- Do not install just any plug-in: check the compatibilities and safety notes first.
Also, and this is perhaps the most important factor, always keep your scripts and CMS up to date. The latest software package usually contains fixes for bugs and security issues from the previous version. Remember to make a backup of your data before any update!
Tip #3: Perform Regular Folder and Control Panel Checks
Sometimes hackers sneak into your site, and can do a lot of damage behind them: spoofing, media files containing viruses, executables and recoded web pages, etc.
Check your folders regularly, at least once every two weeks, to make sure there are no issues with your files.
If you spot any files you don’t recognize, delete them immediately. If that doesn’t work, contact your web host and get help (this is when you need a good hosting company the most). In such cases:
- Change your admin panel password (and username, if possible)
- Check all files to see if they have been damaged.
- If you have an antivirus installed, run it.
Tip #4: Secure Authentication
While familiarizing yourself with cryptography is not essential here, you should start by learning how to use simple and proven multi-factor authentication tools:
Why do you need multi-factor authentication?
You will need to know your user name, your password AND your user code to access your site and content; otherwise, you will be denied access. This can be sent to your phone so that no one but you can access the site.
If you can, find an expert to tutor you as you grow your knowledge of web security, or use online tutorials and courses.
Tip #5: Beware of DDoS Attacks
Distributed Denial of Service (DDoS) attacks are fast-moving and dangerous, as are hacking into servers and replacing your services with fraudulent ones.
A DDoS attack on a server will cause its core services to malfunction, and the entire system will no longer be available to end users.
Read also: What is the best DDOS protection for your website?

What can cause a DDoS attack
- An open network configuration
- Apps with bugs and not updated
- Insecure server configuration
- No maintenance and/or monitoring of network activity
Inform your ISP and hosting provider of this form of attack. The latter can configure each server with a list of alternate DNS addresses, so that when the default DNS becomes unavailable, the whole site still works.
A hacker can only achieve his goals when he manages to block ALL the servers on the list. Another countermeasure can be filtering out all incoming packets with unusual delays and/or high-risk IP addresses. Your host should be aware of denial of service attacks, so talk to them about preventing DDoS attacks.
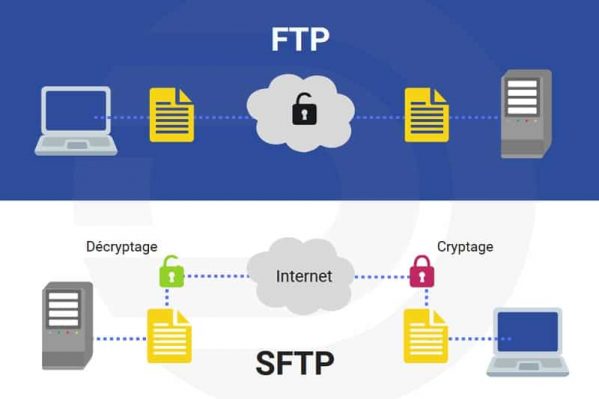
Tip #6: Secure FTP Access with SFTP
Nothing changes for you, it works like normal FTP, but SFTP, or Secure FTP, offers many security benefits:
- It uses SSH to encrypt data and commands during file transfer.
- It uses the client’s server public keys to validate the server when connecting, to ensure that it is not a middleman.
- It is impossible for a hacker to monitor your network traffic.
The problem with the usual FTP command is that it is not encrypted: all downloads to and from the server are transmitted as clear data.
To access FTP via the command line (if you are using Unix/Linux/Mac OS) you can use sftp username
host or simply download a free FTP program that supports SFTP, such as FileZilla (open source).
Tip #7: Learn more about SQL injection to protect against it
Beware of this hacking method, keep your scripts up to date and contact the script developer immediately if you encounter any security breach. Here’s how to perform a simple test:
- Enter the following SQL code in your web form (username and password):
‘ OR ‘t’=’t’; —
which becomes, at SQL level:
SELECT * FROM users WHERE userid=’admin’ AND password= “”. OR ”t’=’t’; — “
- Does it return the contents of your database?
The code could work (we use the conditional because with a bit of luck you have installed a very safe script), since t’=’t’ is a mathematically true statement, so the SQL query will always be executed.
A savvy hacker can construct very elaborate SQL statements to achieve their goals, so be sure to contact the script developer and get help if the script you are using is easily attackable. Or change script.
Tip #8: Regularly Check Your Admin Panel Logs
Your admin panel (cPanel, Plesk, etc.) comes with built-in tools for traffic analysis, access, and security logs that you should monitor at least once a week.
If you use cPanel, we recommend that you check your Analog Stats tool regularly, as it displays a detailed report with:
- HTTP requests
- Monthly, daily and hourly traffic activity reports
- The referrers, browsers and operating systems your traffic is coming from
The logs tools are the first ones you should check when you suspect your website has been attacked.
Attention certains hébergeurs comme Hostinger par exemple, ne vous donne pas accès à vos journaux ou logs serveur !
Tip #9: Make Regular Backups
Back up your files as often as possible. With plugins like Updraft Plus and BackupBuddy, you can set the intervals at which your backups will be performed.
What matters is that you’re constantly downloading new copies of your content, ready to be restored if something goes wrong along the way.

This article has shown you what kind of attacks your website could suffer, and how to combat and prevent them, but your most powerful weapon really is this: backups. This is the only way to restore your site to its original state, as if the hack did not exist.
It is also important to choose a host that offers backup systems on redundant third-party servers!
Bonus Tip #10: Change Your Login URL
If you use WordPress as your CMS, it is possible to easily change the login URL of your administration panel to no longer use /wp-admin.
Via plug-ins like Ithemes Security or the excellent WPS Hide Login from WPServeur, you can make this change in just a few clicks!
Résumé
Finally, here is what you have to do to be up to date with the security of your website:
- Apprendre : le savoir, c’est le pouvoir ! Approfondissez vos connaissances en matière de sécurité et cryptographie, attaques DDoS, injection SQL, les scripts intersites (XSS) et d’autres types d’attaques. Tout ce qui peut vous aider à avoir une vision complète de ce qui se passe lorsque votre site est piraté. Plus vous en savez, plus vous aurez de moyens pour contre-attaquer.
- Tenez-vous au courant : avec des découvertes, des outils et des mises à jour de scripts. Cet article a souligné l’importance de la mise à jour et de la mise à niveau de votre logiciel de site pour assurer une protection plus solide contre les attaques.
- Effectuez des vérifications et des sauvegardes régulières : si vous sauvegardez régulièrement, vous pourrez restaurer !
- Rapport : Lorsque les choses échappent à votre contrôle, signalez les problèmes aux développeurs de scripts et à votre hébergeur. Ils sont là pour vous aider, alors faites appel à leurs services un conseil !
- Learn: knowledge is power! Deepen your knowledge of security and cryptography, DDoS attacks, SQL injection, cross-site scripting (XSS) and other types of attacks. Anything that can help you get a full picture of what happens when your site gets hacked. The more you know, the more resources you will have to counterattack.
- Stay in the know: with discoveries, tools, and script updates. This article has highlighted the importance of updating and upgrading your site software to provide stronger protection against attacks.
- Perform regular checks and backups: if you back up regularly, you can restore!
- Reporting: When things get out of your control, report issues to the script developers and your host. They are there to help you, so call on their services for advice!
IT Security Tips
Software engineering is an interesting field that every good engineer and computer scientist must learn to apply when developing software.
But did you know that it also works the other way around? You, the user, can use concepts from the field of software engineering to make intelligent choices among site software offered to you by developers. You can :
- Understand that a bug can lead to serious hacking of your systems and loss of data.
- Discover the 4 dimensions of reliability and use them to your advantage: availability, reliability, safety and security.
- Identify all your possible security issues: loss of sensitive/important data, failure of certain services, high reconstruction costs (time, money).
Questions to ask before installing and using a script
Reliability: Can I trust this plugin/software?
- Availability: Is the script easily accessible to me? Is its developer reachable for help?
- Reliability: Does the script work well? Does it have bugs or give me problems when I perform actions relevant to my goals?
- Security: Do malfunctions and bugs seriously affect security and performance?
- Security: Does the software have an integrated security module? Is this something I can handle?
- Repairability: If something goes wrong, can I fix it?
- Maintainability: Am I able to maintain this software on my own?
- Survival: Will the software still work under attack? Can I recover well from the attack?
Vulnerabilities
- Software: bugs, transparent data transmission, errors and public logs.
- Human: weak passwords, unprotected directories, disclosure of sensitive data, lack of system maintenance and updating/upgrading.
